最近 用xp框架发现不是那么好用 有些包还是抓不到 请教了下公司二进制的大佬
成功用frida绕过SSL Pinning 抓取https流量
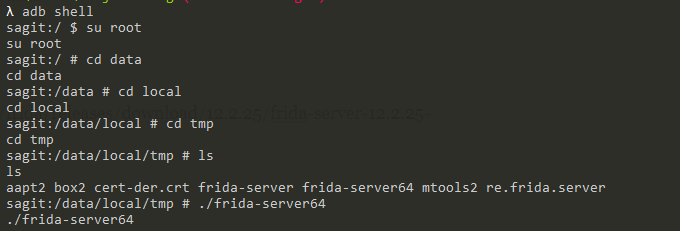
首先需要在手机装 frida-server
https://github.com/frida/frida/releases
安卓手机是小米6
https://github.com/frida/frida/releases/download/12.2.25/frida-server-12.2.25-android-arm64.xz
如果模拟器用x86
然后 adb push进去 以root权限启动
pc端需要装 frida库以及 frida-tools以后应该会用到
写个python脚本抓取 当前应用名
import frida
rdev = frida.get_usb_device()
front_app = rdev.get_frontmost_application()
print(front_app)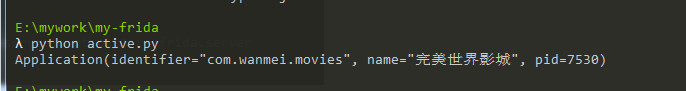
然后用 用绕过SSL Pinning 的脚本 这里面有两个 最新的很简单 但是不知道怎么回事我的手机总是有问题会莫名的卡是 我还是用旧的吧
Java.perform(function() {
var array_list = Java.use("java.util.ArrayList");
var ApiClient = Java.use('com.android.org.conscrypt.TrustManagerImpl');
ApiClient.checkTrustedRecursive.implementation = function(a1,a2,a3,a4,a5,a6) {
// console.log('Bypassing SSL Pinning');
var k = array_list.$new();
return k;
}
},0);旧的代码如下
/*
Android SSL Re-pinning frida script v0.2 030417-pier
$ adb push burpca-cert-der.crt /data/local/tmp/cert-der.crt
$ frida -U -f it.app.mobile -l frida-android-repinning.js --no-pause
<blockquote class="wp-embedded-content" data-secret="gFW10hD5oN"><a href="https://techblog.mediaservice.net/2017/07/universal-android-ssl-pinning-bypass-with-frida/">Universal Android SSL Pinning bypass with Frida</a></blockquote>
*/
setTimeout(function(){
Java.perform(function (){
console.log("");
console.log("[.] Cert Pinning Bypass/Re-Pinning");
var CertificateFactory = Java.use("java.security.cert.CertificateFactory");
var FileInputStream = Java.use("java.io.FileInputStream");
var BufferedInputStream = Java.use("java.io.BufferedInputStream");
var X509Certificate = Java.use("java.security.cert.X509Certificate");
var KeyStore = Java.use("java.security.KeyStore");
var TrustManagerFactory = Java.use("javax.net.ssl.TrustManagerFactory");
var SSLContext = Java.use("javax.net.ssl.SSLContext");
// Load CAs from an InputStream
console.log("[+] Loading our CA...")
cf = CertificateFactory.getInstance("X.509");
try {
var fileInputStream = FileInputStream.$new("/data/local/tmp/cert-der.crt");
}
catch(err) {
console.log("[o] " + err);
}
var bufferedInputStream = BufferedInputStream.$new(fileInputStream);
var ca = cf.generateCertificate(bufferedInputStream);
bufferedInputStream.close();
var certInfo = Java.cast(ca, X509Certificate);
console.log("[o] Our CA Info: " + certInfo.getSubjectDN());
// Create a KeyStore containing our trusted CAs
console.log("[+] Creating a KeyStore for our CA...");
var keyStoreType = KeyStore.getDefaultType();
var keyStore = KeyStore.getInstance(keyStoreType);
keyStore.load(null, null);
keyStore.setCertificateEntry("ca", ca);
// Create a TrustManager that trusts the CAs in our KeyStore
console.log("[+] Creating a TrustManager that trusts the CA in our KeyStore...");
var tmfAlgorithm = TrustManagerFactory.getDefaultAlgorithm();
var tmf = TrustManagerFactory.getInstance(tmfAlgorithm);
tmf.init(keyStore);
console.log("[+] Our TrustManager is ready...");
console.log("[+] Hijacking SSLContext methods now...")
console.log("[-] Waiting for the app to invoke SSLContext.init()...")
SSLContext.init.overload("[Ljavax.net.ssl.KeyManager;", "[Ljavax.net.ssl.TrustManager;", "java.security.SecureRandom").implementation = function(a,b,c) {
console.log("[o] App invoked javax.net.ssl.SSLContext.init...");
SSLContext.init.overload("[Ljavax.net.ssl.KeyManager;", "[Ljavax.net.ssl.TrustManager;", "java.security.SecureRandom").call(this, a, tmf.getTrustManagers(), c);
console.log("[+] SSLContext initialized with our custom TrustManager!");
}
});
},0);frida -U -n com.wanmei.xxx -l universal-ssl-check-bypass.js –no-pause
hook对应的应用名即可
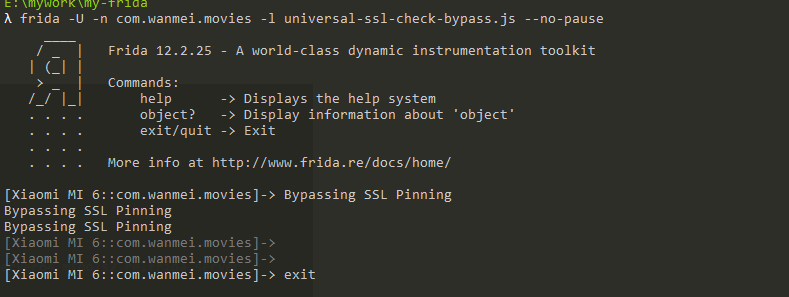
落了两条
要进行端口转发
adb forward tcp:27042 tcp:27042
adb forward tcp:27043 tcp:27043